Private ID verification through Image Steganography on an FPGA
An Overview
Some features of a steganography method:
Embedding capacity - An embedding capacity too small would not be useful to fit a secret message. Images and PDFs are the most popular cover objects for their large embedding capacity.
Imperceptibility - This measurement is required because these methods produce changes in pixel values, image histograms, or generate noise in stego images and it is necessary to keep distortions minimal.
Undetectability - If a steganalysis algorithm detects the inspected media as the stego one, even without knowing any extra information about the secret message, the steganographic approach fails. This is in contrast to encryption, where a successful attack means that the attacker gains access to the decrypted content or partially recovers the encryption key.
Some metrics used to compare methods:
Image histograms - Histogram shift can occur due to changes in pixel values due to the embedding of messages. We can use image histograms to measure the quality of a method[1].
PSNR - Peak signal to noise ration - The ratio between the maximum possible power of a signal and the power of corrupting noise that affects the fidelity of its representation.
SSIM - Structural similarity index - Luminance, contrast, and structure replace the summation method used as the basis for calculating PSNR.
Grayscale vs Color images - Steganographic methods on grayscale images and color images have different effects, in a research conducted [1] the same comparison is done on the grayscale baboon image, the result is PSNR and SSIM agree that the LSB method is better, while the color baboon image produces different values.
Spatial vs transform domain steganography - The transform domain is superior in terms of resistance to manipulation so it is more suitable for use in image watermarking because it can maintain the data embedded in the image container from manipulation damage [1][2][3][4]. Steganography is more focused on imperceptibility, payload capacity, and security.
Application: ID verification
Identity assurance is vital for financial institutions as well as other businesses to determine if they are transacting with legitimate customers.
Fraud, identity theft, and money laundering, among other crimes, continue to threaten these establishments, especially if they fail to implement modern, strong security measures.
Implementing innovative solutions for identity verification and identity document authentication can improve their security measures while providing a seamless user experience and complying with regulations.
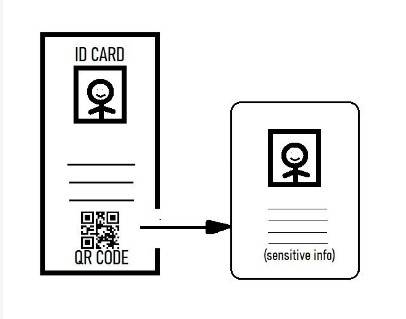
When onboarding new clients or authorizing transactions, businesses can ask their customers to use their mobile devices to take photos of their ID documents such as their passport, driver’s license, or national ID and submit the document image for validation.
Identifying the validity of a client’s submitted documents allows firms to determine forgeries and mitigate potential illegal activities. Moreover, it is essential for anti-fraud regulations.
This write-up is a part of a larger project: Private ID verification through Image Steganography on an FPGA